With the wide application of the QR code access control system, everyone is more and more comfortable with the use of two-dimensional code. For example, many cities can now scan the code by QR code, and the QR code also has its own limitations. Sex, so dynamic QR code, instant effect becomes a safer choice. The access control system has been upgraded from the original card reader to the form of a two-dimensional code reader, which has made the application of the two-dimensional code access control system widely recognized.

Considering that the two-dimensional code access control system is susceptible to many aspects, a higher level of security is required. Compared with the traditional card-type access control, the card can be encrypted for safe use. The entry and exit of the channel through the two-dimensional code is affected by the number of times of entry and exit, the time limit, and the real-time nature of the two-dimensional code. Considering the link between the Wiegand communication protocol and the access controller, the two-dimensional code access control system can better play its role.
Then, how can the two-dimensional code access control system realize the decryption and unlocking through the two-dimensional code? We unveil the principle of unlocking through security and practicality, and then to the user experience.
QR code access control process
Users can register with the WeChat applet and bind their own access controllers to implement user management rights. The use process, just use a small program to automatically generate a dynamic QR code (with timeliness), use this QR code for unlocking the access control, you can unlock the function.
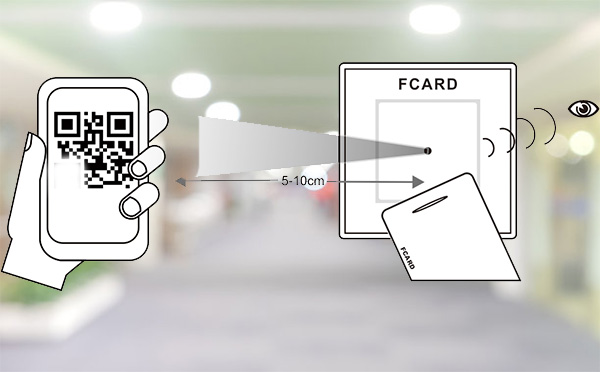
How does QR code access work?
To put it simply, the QR code reader reads a two-dimensional code containing the identity information of the person. The two-dimensional code reader encrypts the two-dimensional code into a digital form and transmits it to the access control through the Wiegand protocol. In this case, the access controller will judge whether it is a authorized person by comparing the information of the previously entered personnel. If the matching is successful, the controller will execute the unlocking command to open the door, and vice versa.
The use of the two-dimensional code access control, from the perspective of the manager and the owner of the community, can not only save the cost formed by the card issuance, but also improve the service level of the cell, so that the user can pass the cell access control faster and save time.
